Hackers Can Read Your Browser Passwords
Trend Micro has an article published in December that is super exciting reading if you're the sort of person who gets excited about revealing all of a user's plaintext Internet passwords during an engagement. I am just that sort of person.
In the article Trend Micro describes an initial infection through a malicious Excel file and an auto open Visual Basic for Applications macro. VBA macro...now you know the story isn't going to have a happy ending and... it doesn't. The macro drops an executable which sets about gaining persistence and communicating to the bad guys command and control system. How it does that is interesting, but I don't have anything to add that isn't covered by Trend Micro.
But check out Figure 11 from the article:
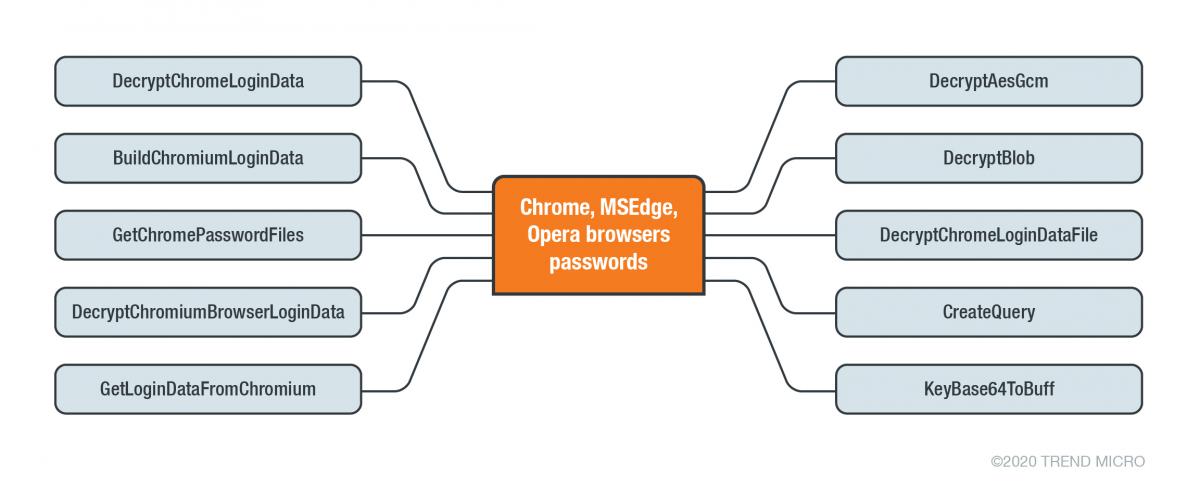 Yeah, that's your browser's saved passwords being decrypted and sent off to the hacker's command and control server!
Yeah, that's your browser's saved passwords being decrypted and sent off to the hacker's command and control server!
Your Chromium based web browser, on Windows at least, uses the DPAPI to encrypt your passwords for storage in SQLiteDB files. This means that to anyone not logged in as you the passwords are mostly inaccessible. But if I can trick the computer into running my program as you then those passwords can be decrypted, exfiled, and used for evil. Chromium based browsers include Google Chrome, Microsoft Edge, Opera, and Brave. The malware also includes stealing Firefox and Internet Explorer passwords though the method is slightly different.
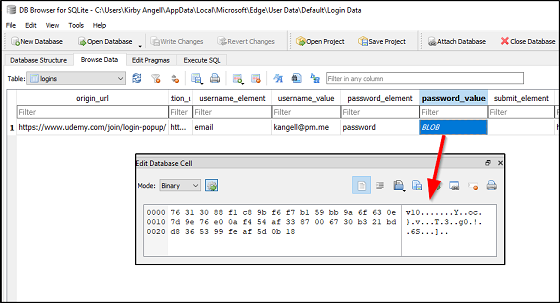
Microsoft Edge storing passwords in an easily readable SQLite file and encrypting with DPAPI's CryptProtectData.
Its fine to think "if someone has access to my computer they are probably going to get all my stuff," but I don't see any reason to make bad guys day's any easier. So lets look at removing all the passwords from the browser and putting them in one of those password apps. As a bonus, we're going to make it just about as easy to enter passwords into webpages as it was before.
KeePassXC
My password app of choice is KeePassXC.
There is a version for each platform I have to use (Windows, Linux, Android, iPhone) and it easily integrates with Chromium based browsers. On a side note: As a pentester my favorite feature of KPXC is that you can configure how many rounds of encryption it does and therefore how long it takes to try 1 password. Brute forcing my KPXC database password just really isn't an option.
You've installed apps before, this one is just like most of those. Click the download link, wait for your virus scanner to bless it, and then double click the installer. Once you have it installed create a database and start putting some passwords in. Next we're going to link it to the browser. Is it hard, you ask? No, its super easy; barley an inconvenience!
Linking to browser
We're going to the "Chrome Web Store" to install a plugin. Yes I know the Chrome Web Store is sometimes problematic. I'm kind of anti-plugin myself due to the obvious chances for evil. So here is the link directly to the KeePassXC plugin published by the KeePassXC devs:
With the plugin installed now we need to tell the KeePassXC app that it is Ok to link to the plugin. Do that by clicking the browser plugin icon and then the blue "Connect" button.
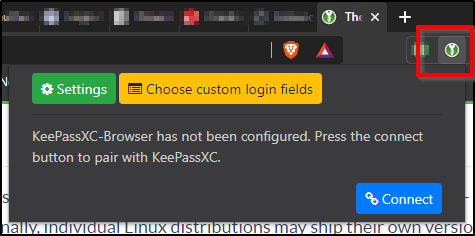
The name you give to the connection doesn't really matter, it just needs to be unique to each browser you authorize to use the database. And that is important, you are authorizing the particular database. If you have multiple databases, you'll need to authorize each of them.
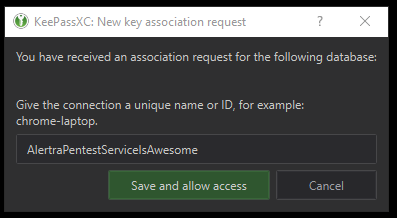
Once you've done that the last step in the setup process is to add a password entry to the database with the URL to the website it goes to. So for instance here is my entry for Alertra's uptime control panel:
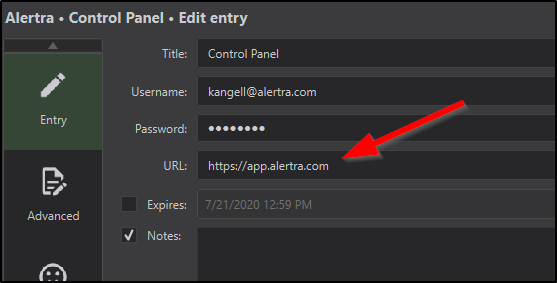
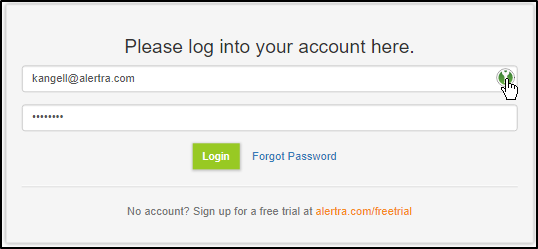
In Use
So now with everything connected up and my username and password in the database, when I go to the Alertra control panel and click the "KeePassXC" icon it automagically fills in the information:
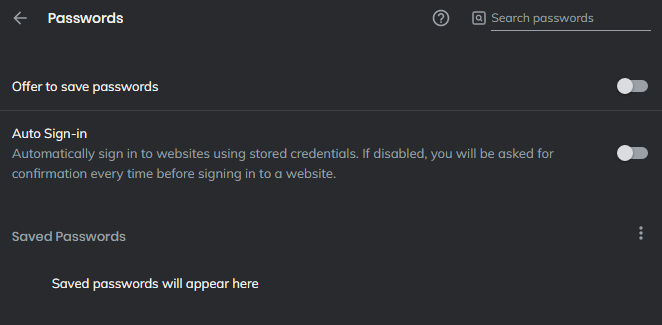
There is some cleanup to do however. We need to get our existing passwords out of the browser. That may be different for each browser. I use Brave and the process goes like this:
- Go to Settings
- Scroll down
- Scroll down some more
- Scroll down a lot more
- Click the "Additional settings" button and scroll even more
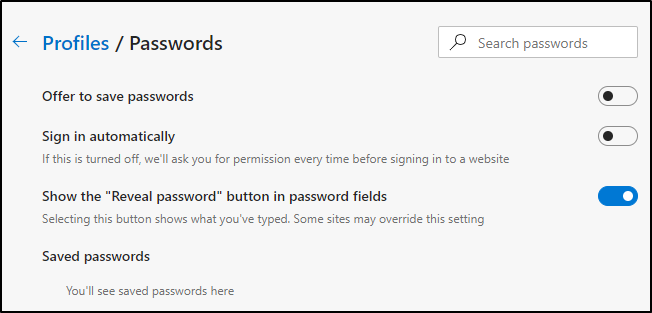
When you get to the "Autofill" section click on "Passwords".
I would manually delete all the passwords first (as you put them into KeePassXC would be a good time) then turn off the ability to save them altogether.
Microsoft Edge is similar, but you just click settings and then "Passwords" without all the scrolling.
Conclusion
Your website passwords sitting at rest in a SQLite database just aren't safe if an attacker can be logged in as you. But if you put them in an encrypted store, such as the one in KeePressXC, then just copying the file won't help anyone. This isn't about 100% absolute safety. There isn't any such thing.
You can be hacked and someone with a lot of time to kill might crack your password file key. It could be that there will be some vulnerability discovered in KPXC either in the way it implements cryptography or the algorithms used. That is all possible. But you know who wont have your all of your plaintext website passwords? The virus author who wrote a snippet of code to copy it from the web browser where most people store that data.
Something like this would really be a thorn in the side of an internal penetration test like the one Alertra does for its customers. We take up the role of a bad guy in an "assumed compromise" test and tell you the answer to the question that keeps you up at night: "If they get in, how bad will it be?" If you want more information about our pentest services you can read about it here.
Author
Kirby Angell is the CTO of Alertra, Inc. and a certified pentester. In addition he has written several articles on Python programming for magazines back when that was a thing. He contributed a chapter to the 1st edition of "The Quick Python Book" published by Manning. He was one of the first 10 Microsoft Certified Solution Developers. Ah the 90s...he probably still has a "Members Only" jacket. He is certified to teach firearms classes in Oklahoma and holds a black belt in mixed martial arts.

Archives:
- April 2022 (1)
- April 2021 (1)
- February 2021 (1)
- January 2021 (2)
- December 2020 (1)
- January 2020 (2)
- October 2019 (1)
- September 2019 (1)
- August 2019 (1)
- July 2019 (1)




















